¶ TLS
¶ What is TLS
Tls is an encryption
way to secure a connection beetwenn two point with asymetric encryption
we not use use the same key to encode or decode
so you need two key the public and the private key
the public key is like a secure door and the private is the key
DO NOT SHARE PRIVATE KEY ITS FUCKING PRIVATE
you can generate a this two key with
ssh-keygen
when you have a key you can go inside a user folder and add youre public key you can have more than 1 key in this file
and you can put your public key inside different cluster node VM ...
vim ~/.ssh/authorized_keys
then you can connect to this user with ssh
ssh -i /path/to/private-key user@name/or/IP
# exemple
ssh -i ~/.ssh/private-key-demo_rsa adm-vaultaire@bastion.local
ssh -i ~/.ssh/private-key-demo_rsa adm-vaultaire@192.168.1.254
¶ openssl
you can also use openssl for gen youre key
more use for website
openssl genrsa -out my-key.key 1024
openssl rsa -in my-key.key -pubout > my-pubkey.pem
we dont talk about certificate this have to come with the key when you use web app its deliver by entity of certification like cert-bot its ensure that the key use is the good one for a website
the certificat contain a lot of information
its also use on ssh communication that why for the first connection to a host you see a message new certificate are you sure
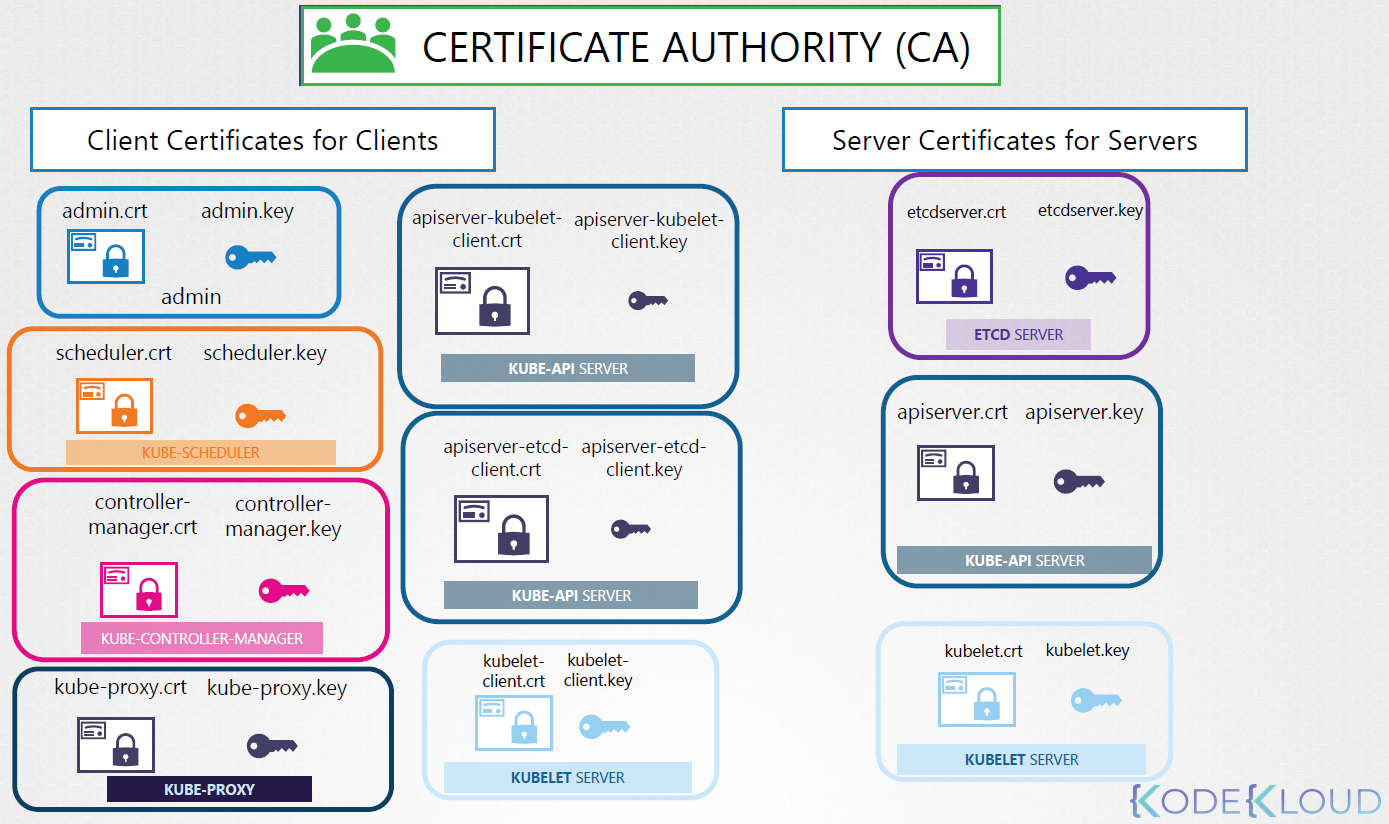
¶ TLS inside Kubernetes cluster
Private = *.key *.-key.pem
Public = *.crt *.pem
All the communication of the cluster have to by secure with tls
¶ https API endpoint
this component expose and https api to external network so we need
- kube api server = apiserver.key and a apiserver.crt the api server need 2 more certificate for etcd and kubelt communication
- ETCD server = etcdserver.key and a etcdserver.crt
not eaven on the master node on all node we have kubelet
- kubelet server = kubelet.key and a kubelet.crt
¶ Kube-APIserver
there are many thing that want to intercat with the api
like admin-user and kube-scheduler so they all need a key and a certificate
same for kube-controller-manager
and the kube proxy need this own key and certificate
with all this info you can be sure that all communication is tls prrof and you can now who did what.
¶ Create signed certificat
¶ Self signed
#Generate key
openssl genrsa -out ca.key 2048
#Certificate Signing request
openssl req -new -key ca.key -subj "/CN=KUBERNETES-CA" -out ca.csr
#Sign Certificates
openssl x509 -req -in ca.csr -signkey ca.key -out ca.crt
¶ Démo for kube-admin user
#Generate key
openssl genrsa -out kube-admin.key 2048
#Certificate Signing request we add a group detail for the certificate
openssl req -new -key kube-admin.key -subj "/CN=kube-admin/O=system:masters" -out kube-admin.csr
#Sign Certificates
openssl x509 -req -in kube-admin.csr -signkey kube-admin.key -out kube-admin.crt
you can follow this for create all the certificate you need but dont forget to adpat you certificate args
¶ Use certificate
you can do it for each request
curl https://kube-apiserver:6443/api/v1/pods --key kube-admin.key --cert kube-admin.crt --cacert ca.crt
or do a config file in yaml
apiVersion: v1
clusters:
- cluster:
certificate-authority: ca.crt
server: https://kube-apiserver:6443
name: kubernetes
kind: Config
users:
- name: kube-admin
user:
client-certificate: kube-admin.crt
client-key: kube-admin.key
¶ View Certificate
you can see the path of the cert for kube-apiserver here
cat /etc/kubernetes/manifests/kube-apiserver.yaml
spec:
[...]
- --client-ca-file=/etc/kubernetes/pki/ca.crt
[...]
- --etcd-cafile=/etc/kubernetes/pki/etcd/ca.crt
- --etcd-certfile=/etc/kubernetes/pki/apiserver-etcd-client.crt
- --etcd-keyfile=/etc/kubernetes/pki/apiserver-etcd-client.key
[...]
- --kubelet-client-certificate=/etc/kubernetes/pki/apiserver-kubelet-client.crt
- --kubelet-client-key=/etc/kubernetes/pki/apiserver-kubelet-client.key
[...]
- --tls-cert-file=/etc/kubernetes/pki/apiserver.crt
- --tls-private-key-file=/etc/kubernetes/pki/apiserver.key
for get info of crt
openssl x509 -in /etc/kubernetes/pki/apiserver.crt -text -noout
¶ CA authority
for signed a certificate you need a CA (certificat authority)
in kube its the master node
if you want a better CA manage there is a certificate API
you can use this api to signed with api request to signed a certificate
with rhis api you can
review request
approve requests and share certs
Démo
#first a user gen a key
openssl genrsa -out test.key 2048
openssl req -new -key test.key -subj "/CN=test" -out test.csr
# Now the admin take the csr and generate a request
cat test.csr | base64 > akshay-base64.csr
cat test-crt.yaml
---
apiVersion: certificates.k8s.io/v1
kind: CertificateSigningRequest
metadata:
name: akshay
spec:
groups:
- system:authenticated
usages:
- digital signature
- key encipherment
- server auth
signerName: kubernetes.io/kube-apiserver-client
request: "paste contetn of akshay-base64.csr"
#to see the request
kubectl get csr
#and approve
kubectl certificate approve test
#now you share the csr with the user
kubectl get csr test -o yaml #you see the crt in a base 64
the csr | base 64 --decode
#and you share
# for denied a request
kubectl certificate deny request-name
kubectl delete csr request-name